PSA: Highly Critical Drupal Core Vulnerability Impacts Over 1 Million Sites
Yesterday the Drupal security team announced a highly critical unauthenticated remote code execution vulnerability in Drupal core. The vulnerability allows an attacker to leverage multiple attack vectors and take complete control of a website. The Drupal team estimates that, at the time of the announcement, over one million sites are affected – about 9% of Drupal sites. They also reported that, to their knowledge, it was not being actively exploited.
This post is Copyright 2018 Defiant, Inc. and was published on the wordfence.com official blog. Republication of this post without permission is prohibited. You can find this post at: https://www.wordfence.com/blog/2018/03/drupalgeddon2/
We normally don’t cover Drupal vulnerabilities on this blog, but given the nature and scope of the issue, we felt compelled to help spread the word via this public service announcement (PSA).
Site owners should upgrade to a safe version of Drupal core immediately. While the reports of no active exploits are comforting, the announcement will draw a lot of attention from attackers. Given the nature of the vulnerability, there will literally be a race between site owners upgrading and attackers figuring out an exploit.
Here is a high-level summary of the versions impacted and recommended actions:
- Sites running Drupal 8.x should update to version 8.5.1
- Sites running Drupal 7.x should update to version 7.58
- There are patches available for 8.3.x and 8.2.x versions
- Sites running end of life versions will need to upgrade to a supported version of Drupal
A more detailed overview of upgrade recommendations from the Drupal security team is available on Drupal.org. They have also published a detailed FAQ.
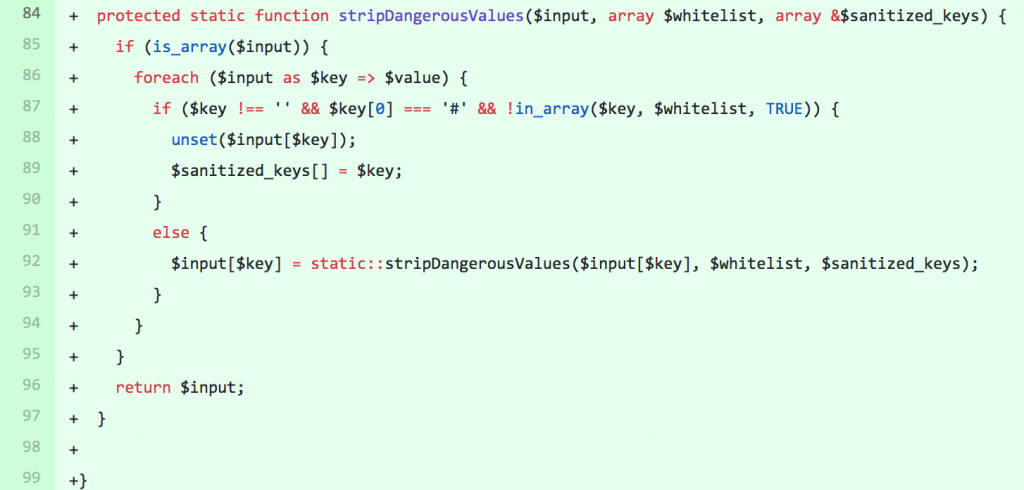
Looking at the diff of the patches provided by the Drupal team, they reveal a new DrupalRequestSanitizer class used to sanitize user input.
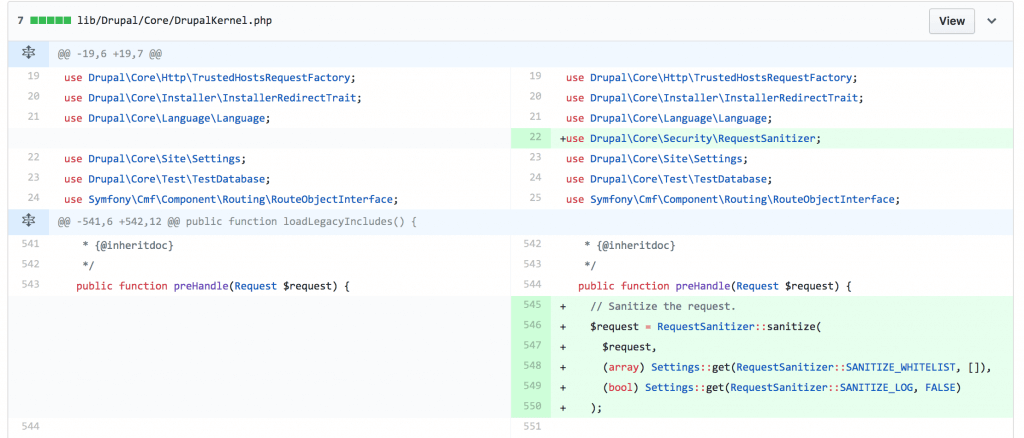
This class is used to filter values from the query string, post body, and cookies that begin with #.
A proof of concept demonstrating the attack has not yet been made public, but we expect that one will be made available soon.
This attack has been nicknamed “Drupalgeddon 2.” The previous Drupalgeddon was as high in severity as this, and had automated attacks against unpatched Drupal sites within a matter of hours after the public announcement of the vulnerability was made.
Please help us spread the word about this potentially nasty vulnerability to other site owners so they can stay a step ahead of attackers.
The post PSA: Highly Critical Drupal Core Vulnerability Impacts Over 1 Million Sites appeared first on Wordfence.